The Kazakhstan government has once again issued an advisory to all major
local Internet Service Providers (ISPs) asking them to make it
mandatory for all their customers to install government-issued root
certificates on their devices in order to regain access to the Internet
services.
The root certificate in question, labeled as “trusted certificate” or “national security certificate,”
if installed, allows ISPs to intercept and monitor users’ encrypted
HTTPS and TLS connections, helping the government spy on its citizens
and censor content.
In other words, the government is essentially launching a “man in the middle” attack on every resident of the country.
But how installing a “root certificate” allow ISPs to decrypt HTTPS connection? For
those unaware, your device and web browsers automatically trust digital
certificates issued by only a specific list of Certificate Authorities
(CA) who have their root certificates installed on your system.
Therefore compelling Internet users into installing a root certificate
that belongs to a Government Organisation gives them the authority to
generate valid digital certificates for any domain they want to
intercept through your HTTPS traffic.
Starting from April this year, Kazakh ISPs began informing their users
about the “national security certificate” that would be mandatory to
install in order to continue uninterrupted access to a list of “allowed”
HTTPS websites.
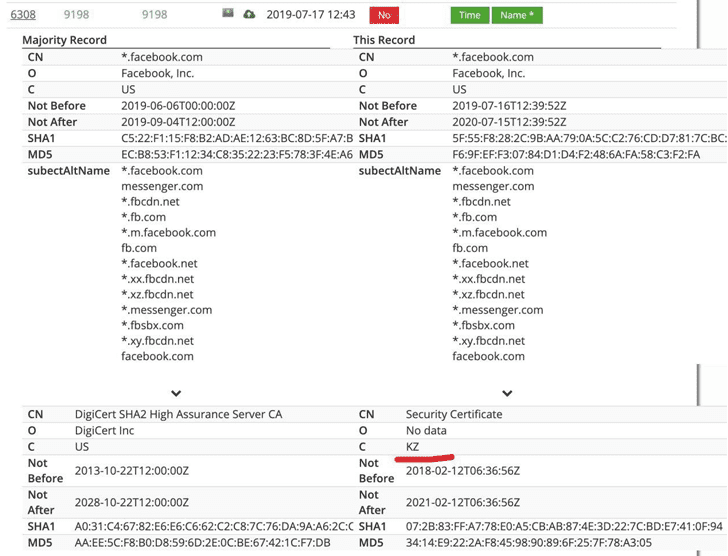
Now, Tele2, one of the major Kazakh ISPs, has finally started redirecting all HTTPS connections of its customers to a web page containing certificate files and instructions on how to install it on Windows, macOS, Android, and iOS devices.
One of the most serious security implications we can easily spot
here is that — since users can only browse non-HTTPS sites before
installing the certificates, the Cert files are available for download
only over insecure HTTP connections, which can easily allow hackers to
replace Certificate files using MiTM attacks.

Other national ISPs, listed below, also have plans to start forcing their Internet users into installing the root certificate shortly to comply with the law.
The controversial advisory has been issued with respect to amendments to the Law on Communications 2004 (the “Communications Law“) that the Kazakhstan government passed in November 2015.
According to Clause 11 of Article 26, the “Rules for Issuing and
Applying a Security Certificate,” all national communications service
providers are obliged to monitor the encrypted Internet traffic of their
customers using government-issued security certificates.
The law was intended to come in force starting 1 January 2016, but the
Kazakhstan government failed to force the local ISPs following a series
of lawsuits.
It seems now the Kazakhstan government is making another attempt to
force the amendments, putting privacy and security of millions of its
citizens at risk from both hackers and the government itself by breaking
the fundamentals of Internet security protocol.
According to the note displayed by Internet providers, the amendments have been forced “in connection with the frequent cases of theft of personal and credential data, as well as money from bank accounts of Kazakhstan.”
“A security certificate has been introduced that will become an effective tool for protecting the country’s information space from hackers, Internet fraudsters and other types of cyber threats,” the note reads.
“The introduction of a security certificate will also help in the protection of information systems and data, as well as identifying hackers and Internet fraudsters before they can cause damage.”
“It will also allow Kazakhstan Internet users to be protected from hacker attacks and viewing illegal content.”
From these statements, it’s evident that the Kazakh government wants to
take control over what content their citizens should be allowed to view
on the Internet and also to turn Kazakhstan into a deep surveillance
state.
Also, since half of the education is more dangerous than no education, I
find it very concerning that ISPs are promoting “custom CA root
certificate installation” as a better solution that boosts online
security.
The pages and press releases created by ISPs with instructions on “why
and how to install the government-issued certificate” doesn’t correctly
explain the threat of installing a wrong root certificate.
It littery leaves the majority of citizens at risk of social engineering
attacks, and an opportunity for hackers to trick users into installing a
malicious root cert from unofficial websites and sources.
Besides this, intercepting HTTPS communications will also allow ISPs to
inject advertisements or tracking scripts on all web pages users visit.